
A few weeks ago, I was asked by a viewer of my YouTube channel (“Cryptography for everybody”) if there was an “affine cipher component” in CrypTool 2. After taking a look at all our components, I realized that there was no component that implemented this cipher. I made a video for new CrypTool 2 developers and how they may implement the affine cipher, as an example of how to build new CrypTool 2 components. But I never added such an affine cipher component to CrypTool 2. So I sat down and created a brand new component and also made a YouTube video about the cipher (see the video at the end of this blog article). Also, in this blog article I summarize the video and how the encryption process works. You’ll also learn about the size of the key space and the unicity distance of the affine cipher. I hope you enjoy reading the article and that you understand how the cipher works afterwards.
1. Introduction to the Affine Cipher
The affine cipher is essentially a monoalphabetic substitution cipher, which means each letter of the plaintext is substituted with another letter to form the ciphertext. This method can trace its origins back to the time of the Caesar cipher, a cipher used in ancient Rome.
Over the course of history, as the mathematical domain grew, so did the complexity and strength of ciphers. The affine cipher is a one of the first testaments to this growth, combining the principles of two basic ciphers: the additive and the multiplicative cipher.
An interesting aspect of the affine cipher, and the ciphers we’ll be discussing, is that they operate on numbers. The ciphers essentially translate each letter of the used alphabet (e.g. the Latin alphabet) into a number (and back), providing a platform for mathematical operations. This translation is quite straightforward:
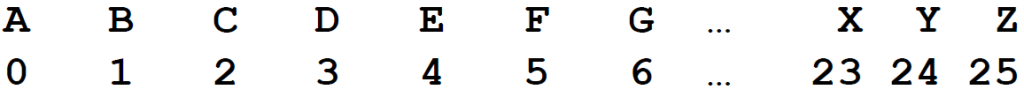
2. The Additive Cipher
Let’s start with the basics. The additive cipher functions by adding an offset number to each letter, shifting it to the right. This is the underlying principle behind the famous Caesar cipher.
For this cipher:
- Key: The shift value, denoted as
𝒃 - Encryption:
𝑐 = (𝑝 + 𝑏) 𝑚𝑜𝑑 26 - Decryption:
𝑝 = (𝑐 - 𝑏) 𝑚𝑜𝑑 26
For example, consider a shift value (b) of 5:
Plaintext: HELLO WORLD = 7 4 11 11 14 22 14 17 11 3
Ciphertext: MJQQT BTWQI = 12 9 16 16 19 1 19 22 16 83. The Multiplicative Cipher
The multiplicative cipher involves multiplying each letter with a specific number. This process essentially “randomly selects” a letter from the alphabet, but still for each plaintext letter always the same ciphertext letter.
Key elements:
- Key: The multiplication value, denoted as
𝒂. However, there needs to be an inverse (𝑎⁻¹) of this value for decryption. For a number𝒂to have a multiplicative inverse modulo m (here the alphabet size, which is 26),𝒂and m must be coprime, which means their greatest common divisor (GCD) is 1. In mathematical terms: gcd(a,m)=1. - Encryption:
𝑐 = (𝑝 ∙ 𝑎) 𝑚𝑜𝑑 26 - Decryption:
𝑝 = (𝑐 ∙ 𝑎⁻¹) 𝑚𝑜𝑑 26
To illustrate, let’s use 𝑎 = 5 (with its inverse 𝑎):⁻¹ = 21
Plaintext: HELLO WORLD = 7 4 11 11 14 22 14 17 11 3
Ciphertext: JUDDS GSHDP = 9 20 3 3 18 6 18 7 3 15Note: Computing the inverse of a number in modular arithmetic is crucial. Techniques like the extended Euclidean algorithm (see https://en.wikipedia.org/wiki/Extended_Euclidean_algorithm) come in handy, and we’ll delve into this in a future discussion (and youtube video :-))!
4. The Affine Cipher
Building on the previous concepts, the affine cipher is a combination of both additive and multiplicative ciphers.
Key components:
- Key: Comprises a multiplication value
𝒂and a shift value𝒃. - Encryption:
𝑐 = (𝑝 ∙ 𝑎 + 𝑏) 𝑚𝑜𝑑 26 - Decryption:
𝑝 = (𝑐 − 𝑏) ∙ 𝑎⁻¹𝑚𝑜𝑑 26
For a hands-on example, using 𝑎 = 5 (inverse 𝑎) and ⁻¹ = 21𝑏 = 5:
Plaintext: HELLO WORLD = 7 4 11 11 14 22 14 17 11 3
Ciphertext: OZIIX LXMIU = 14 25 8 8 23 11 23 12 8 205. Keyspace Size and Unicity Distance
Understanding key spaces and unicity distances is essential for appreciating the security of a cipher:
- Keyspace size: For the affine cipher, we have
25possible values for𝒂and26for𝒃. However,𝒂and26need to be coprime. Thus, only specific values are valid for𝑎as they possess an inverse (𝑎). These values are⁻¹1, 3, 5, 7, 9, 11, 15, 17, 19, 21, 23, and 25. The total key space is then12 x 26 = 312. - Unicity distance (𝑈): This concept helps determine the number of characters required to uniquely identify plaintext from its ciphertext. For the affine cipher, using the entropy of the key space (
𝐻(𝐾)) and the redundancy of the English language (𝐷), the unicity distance is approximately3. The equation to compute the unicity distance is U = H(K)/D.
In essence, the affine cipher, with its mathematical underpinnings and historical significance, offers an exciting glimpse into the world of cryptography. Whether you’re a beginner or an aficionado, diving into these ciphers can be both intriguing and rewarding. Stay tuned for more cryptographic adventures also with CrypTool 2
6. A YouTube Video About the Affine Cipher
Of course, I also made a YouTube video about the affine cipher. You may watch it here:
