On Saturday the 23rd July 2022, the Maritime Radio Historical Society (MRHS) and the Cipher History Museum sent an Enigma-encrypted radio transmission via the KPH stations. I was able to receive the message and decrypt it using CrypTool 2. Message was sent via Morse (CW) frequencies and radioteletype (RTTY) frequencies.
In one of my YouTube videos, I explain how I received the message using KiwiSDR and how the Morse decoding in KiwiSDR and the decryption process in CrypTool 2 worked. I thank Tom Perera from the cryptocollectors group for providing the playbacked parts of the original audio recording of the transmission. Finally, I recorded the wrong audio device, thus, I only had the video recording of what I did.
Despite not being the fastest decipherer, I am proud that I received a very nice certificate. I got it after sending the plaintext to the Martitime Radio Historical Society via email:
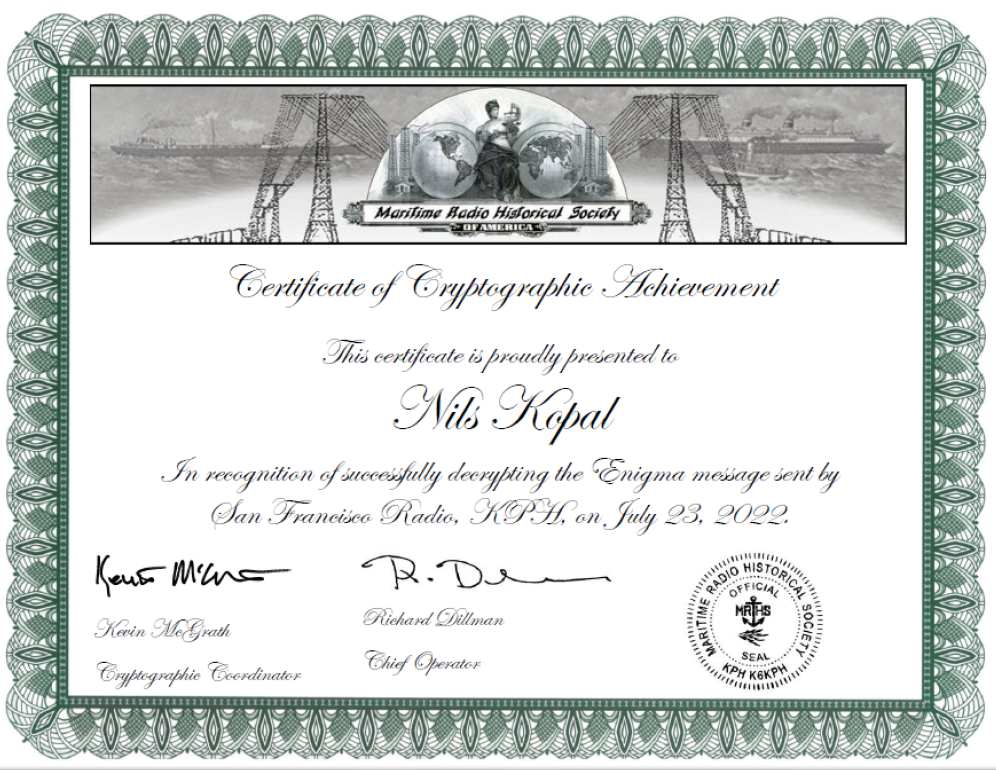
If you want to try to decrypt the Enigma message on your own, here is my received and Morse-decoded message (actual ciphertext in bold):
FQ CQ DE KPH KPH KPH CQCQ CQ DE KPH KPH KPH CRYPTO MESSAGE FOLLOWS bt HQTRS FR FOCH 1914Z bt 100 bt BRV LTV bt VCXTY JRVHA NNKMO FGKIG OIPLM KVHVZ WDMIP XWRBX JKDWT KGZZA IWJVN QUTJF HPPWG KEDDQ QFEMT UKMQU IDIGF YUAJB RPPWS IBJCV EI[err][err]E CQ CQ CQ DE KPH KPH KPH CQ CQ CQ DE KPH KPH KPH CRYPTO MESSAGE FOLLOWS bt HQTRS FR FOCH 1914Z bt 100 bt BRV LTV bt VCXTY JRVHA NNKMO FGKIG OIPLM KVHVZ WDMIP XWRBX JKDWT KGZZA IWJVN QUTJF HPPWG KEDDQ QFEMT UKMQU IDIGF YUAJB RPPWS IBJCV E 5IH[err][err][err][err]EN SVAM bt I[err]
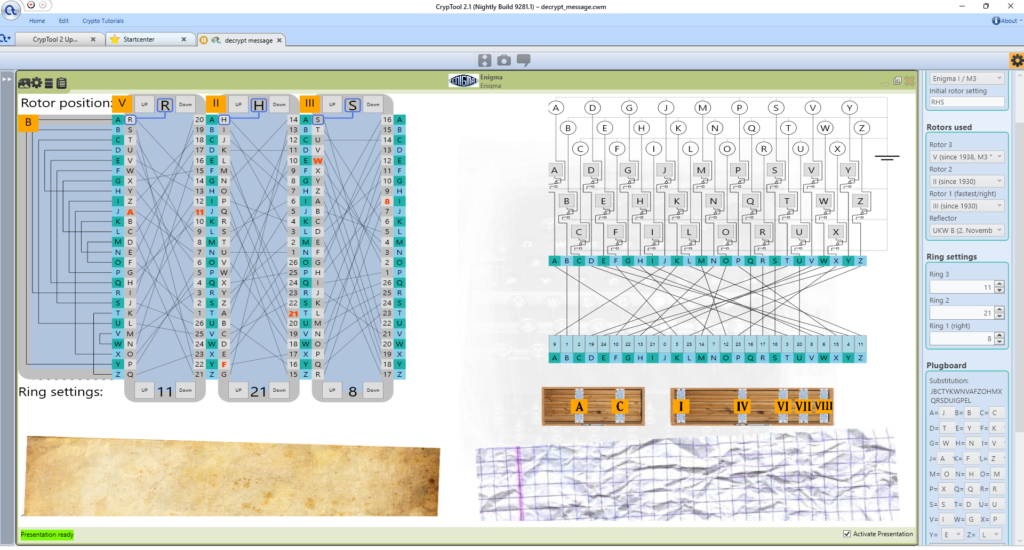
You can decrypt it using CrypTool 2 or any Enigma simulator. Here is a screenshot of the Enigma and settings in CrypTool 2:
Some references:
– To visit the MRHS, please go to: https://www.radiomarine.org
– The Cipher History Museum go to: https://cipherhistory.com/
– KiwiSDR you can find here: http://kiwisdr.com